
What the end of Windows 7 REALLY means
Today marks the last day that Microsoft will provide updates for the Windows 7 operating system. Depending on who you talk to, your computer may
Learn more about what we do and how we help companies just like yours!

Today marks the last day that Microsoft will provide updates for the Windows 7 operating system. Depending on who you talk to, your computer may
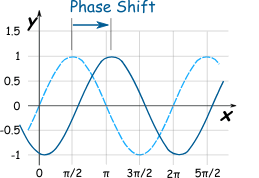
If your business and technology planning are out of sync, it may be time for a technology phase shift. Fortunately technology capability is not cumulative,

The DIY (do it yourself) movement has taken off with the advent of social media. Pinterest runs an entire business off of it! The two

Microsoft Teams is fast becoming the go-to application for managing communication and information flow within organizations. We wrote HERE about how Teams will be supplanting

It is time to shift your focus from managing devices to managing your data. The threat landscape changes quickly but the target remains the same,
Cybersecurity has finally been elevated to a “standard” in the business world. A business of ANY size needs to have a cybersecurity as part of

MFA is no longer optional in today’s threat landscape. Over three YEARS ago we started talking to our Clients about utilizing MFA, as passwords are

The first step to improve your business productivity is to understand the three illusions executives have about internal IT versus outsourcing. These illusions are reinforced

Netflix has changed the way we consume video content, and grown into a streaming giant. A key to their success was knowing what parts of

Congratulations, you are part of a growing business that is about to make an acquisition! All the financials are thoroughly reviewed, corporate culture is synergistic,

Large technology companies are masters of technology consolidation, think Microsoft, Salesforce, and Apple. They watch new technologies emerge from other groups, and then buy or

Email is the defacto communication standard in business today. This is interesting considering the first email sent was in 1971, and the fax machine has

If what physical device you are using determines what applications and services you have access to, it’s time to reevaluate your technology setup! It still

Digital natives will not hang around long with a company that still things the world is flat! This shift of mentality is real and happening

Debt refers to the state of owing something, usually money, to another party in the future. Technical debt is when you “borrow” from your company’s

Delegating is a key driver for growth and scalability in your business. You can’t do it all! Delegation does not remove responsibility, so you still
[vimeo 314332980 w=384 h=339] There is a time limit in sporting events is because there has to be a loser! Don’t put a time limit
[vimeo 313262571 w=384 h=339] Technology is NOT always the answer to your business needs or issues. In the video we discuss four common areas where

Client retention is an important metric for any business, especially those with a high customer acquisition cost (CAC). The old saying it’s always easier to

First, no technology platform provides 100% uptime, period. Technology is too complex for that level of reliability. The car has been around for about 120

Do you run your technology like a plane, train, or automobile? All three will get you from point A to point B but in different

Go ahead and reread the headline again; it’s correct. We have reached the limit of technology, making us more productive, and entered the era of

Would you build a power or water filtration plant for your business? The answer for 99% of us is no, which would make no sense. Many

The technology space is known for innovative, rapidly growing companies. The downside is finding your technology provider has moved “upmarket” and left you behind. This
Many groups provide a weekly, Onsite IT “visit” to make sure that their customer’s technology is working properly. This is based on an hourly billing

Making a decision is the first step towards maximizing return. Until that happens, we are operating in the theoretical world, not reality. Once you have

How is making a decision about what to purchase for dinner different from buying a new car? Those differences are pretty obvious. What about the

Business is all about making good decisions and then executing them. Deciding what products and services your business buys is a key driver of your

Is the first item you review when making a decision the cost? Do you think in terms of what you can (or can’t) afford? When

Productivity growth in the US has stalled out over the past several years. Productivity is the measure of output in good or services per hour

A good partner can make a big difference in the performance of your INTERNAL teams. Finance partners with accounting firms, legal with outside council, and

We have all heard the adage, “it takes money to make money”, and this holds true even with technology. Lack of proper investment in technology

If you wanted a reliable source of milk back in the day, you owned a cow. There was no reliable distribution network or steady supply

The emergency room is the last place anyone wants to be. It means that something unplanned and usually painful has occurred. To make matters worse,

When you have no plan, everything seems like a good idea. Think about that for a minute. How many times in your business do you

Your business should be unique in some way. It’s what we call a competitive advantage. If there is no uniqueness, you compete on price, which

Congratulations, you are a growing company, and now it’s time to hire an IT Director. Or is it? This role has evolved significantly over the

Your business reputation is important; you should protect it properly and train your people! Years of work go into building it, but it only takes

The new business initiative has been planned and deliverables defined, but why did it not product results? Often, we define deliverables that actually don’t tie

The goal of life in many ways is to be comfortable. Comfort can in financial, health, or physical aspects of your life. This should never

We all know the feeling of taking “time off” and wondering how much work we can fit in during the vacation. Spring Break is mandatory

“Those younger folks handling our technology, they know how it works,” says the business owner who has delegated all technology decisions to anyone under 30.

The shift from processing “information” to gathering “intelligence” in your business is critical to long term success. There is a big difference. Intelligent Technology is a

Does your business need an Intelligent Technology transformation? Not just a new coat of paint, but a serious remodeling. Like that starter house you bought,

Doing more with less, also known as increasing productivity. This important concept is how employees enjoy a higher standard of living due to increased wages,

Would you rather have consistent results or random flashes of greatness? Do you want a business that improves over time and is managed with the
Ever driven down the road in a car that was out of alignment? When you let go of the wheel, the car starts going in

The shift from processing “information” to gathering “intelligence” in your business is critical to long term success. There is a big difference. Intelligent Technology is

How to increase profit of your company or department is usually the #1 Goal of Business Owners and managers. The best way to do this

“Am I getting what I’m paying for?” This is a question every business leader should ask themselves about each their budget lines items at least