Identifying Ideal Healthcare Partnerships: What You Need
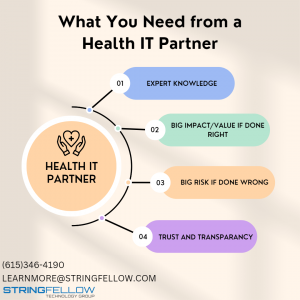
As a healthcare C-level executive or office manager, identifying ideal healthcare partnerships can be an infrequent yet crucial part of the growth and success of your organization. In a rapidly evolving healthcare landscape, collaborating with the right partners can bring significant value and impact, while choosing the wrong ones can pose substantial risks. Through […]
Stringfellow Podcast Episode #1

Did you know we had a Stringfellow podcast at Stringfellow Technology Group? Listen to us on the go and mobile Spotify here: #technology #podcast #healthcare #healthcareit https://open.spotify.com/show/1VujjBlVAY3TIyBysZgskL
March 2023 Webinar – Planning for Success: Using Teams to Implement Traction, Planner and Todo
Link to Video Join Edward and Daniel this month as they discuss using Microsoft Planner and To Do to improve business productivity. They pull from examples of how it’s used at Stringfellow Technology Group and how they’ve implemented Traction to become more productive.
5 Ways to Stay Focused When Working from Home

As more and more people shift to remote work, staying focused while working from home can be challenging. With distractions such as social media, household chores, and family members, it’s easy to lose track of time and miss deadlines. However, with some simple strategies, you can boost your productivity and stay focused while working from […]
Don’t Use RFPs When Searching for Healthcare Managed IT Services

Why You Need a New Approach to Find the Right Healthcare Managed IT Services Outsourcing your IT services as a multi-site healthcare group can help you streamline your operations and save money. However, choosing the right IT partner is crucial for your business’s success. One common approach to finding a suitable IT partner is to […]
Maximize Healthcare Cashflow: Technology Workflows to Improve Reimbursements

Small healthcare providers are working on outdated technology workflows and need an improvement to maximize healthcare cashflow. The old way increases the time to create and process claims, which has a direct effect on revenue. As an independent healthcare provider, having payors reimburse correctly and on time is critical to cash flow. Proper technology workflows […]
Positive Client Reviews

We love getting positive client reviews about our support team. When’s the last time you had a great experience with tech support? With over 98% customer satisfaction rating for the last year, we value our customers and how they experience service and support. When is the last time you talked to a better IT partner? […]
Insourcing vs Outsourcing: Pros and Cons of Technology Paradigms

Technology is essential to every company’s success in the modern business world. Today, a company’s capacity to adapt and stay ahead is impacted by its technology team, whether internal or outsourced. This blog article will examine several technology leadership strategies and weigh the advantages and disadvantages of hiring technology staff internally versus externally. Do It […]
Why Managed IT Services in Healthcare Are So Important

Due to the sensitive nature of their client’s data and information, healthcare organizations are most likely to benefit from managed IT services than businesses in other industries. Managing a complex IT infrastructure takes an incredible amount of dedication and expertise, which is exactly what an MSP (managed service provider) can do for you and your […]
It starts with a notification…

A notification in your pocket dings and lets you know someone is trying to log into your email. That’s weird, you think, I didn’t do that. Upon closer inspection, you notice the login request is coming from Paris, France. Something’s not right. A hacker phished You. The excel spreadsheet that your work colleague sent you […]
Disaster Recovery Services: What Are They and Why They’re Necessary

Disaster planning within the healthcare industry, or any industry for that matter, is a lot of hoping for the best while preparing for the unexpected. Part of that preparation is assembling some form of a plan for when the inevitable happens. This is where disaster recovery (DR) and disaster recovery services come in. What is […]
MS Teams Status Message Ideas

MS Teams status message ideas are a great way to boost productivity and give standard answers to coworkers and colleagues. Staying connected and productive is more crucial than ever in the fast-paced work world of today. One of the best ways to accomplish this is by utilizing MS Teams. Teams is a potent collaboration platform […]
Healthcare Business Technology Goals for 2023

What are your healthcare businesses technology goals for 2023? Here is a list of items you may consider for your multi-site clinic technology needs. Implementing an electronic health record (EHR) system can assist a medical clinic. They do this by streamlining and improving the administration of patient medical records, appointments, and billing. Surely by now […]
How to Protect Yourself from Internet Hoaxes 101

Cybersecurity is a fast-changing, stressful, and downright scary space to play in. The number and sophistication of cyberattacks are on the rise as hackers continue to outsmart preventive security measures and seep into our environments. It’s becoming evident that navigating how to protect yourself from internet hoaxes and cyber crimes is more challenging than it […]
The Future of AI in Healthcare: A 2024 Perspective

As we approach the end of 2023, the transformative power of Artificial Intelligence (AI) in the healthcare sector is becoming increasingly evident. From enhancing patient care to streamlining administrative tasks, AI is poised to redefine the future of medical practices. Partnering with industry leaders like Stringfellow Technology Group can help healthcare groups harness the full […]
Healthcare Technology Challenges in 2023

As we move into 2023, healthcare technology challenges should not keep your clinic from success. One of the biggest challenges is the growing need for more advanced and sophisticated technology to support care delivery. Healthcare IT makes or breaks an outpatient clinic. As the population continues to grow and age, the demand for healthcare services […]
Making Money Work for You: Budgeting for IT Growth

Watch the Full Video of this Webinar Good morning. My name is Daniel Buchanan and this is June and July’s webinar for Stringfellow Technology Group. So you’ve come to the right place if you wanna learn a little more about making money work for you. We want to cover a wide range of topics that […]
4 Motivators for Stuck Tech Projects
4 Motivators for Stuck Tech Projects Technical people tend to focus on details. And when it comes to technology consulting there are a lot of details. For example, the minimum system requirements for a server, the firewall ports that are required for an application, the space included in a wireless network. Technical people juggle technical […]
Five Ways Your Team Can Boost Productivity with Azure AD

Everyone wants a more productive team, but with Azure AD you can deliver a lot of time saving benefits without much additional cost or another server. You may not recognize Azure AD as something you use, but if you use Microsoft 365, you’re already in Azure and you’re already using Azure AD. Azure AD is […]
Keep the I, outsource the T

IT is two separate and distinct areas, Information, and Technology. Most organizations only focus on the “T” resulting in reduced profits and productivity. Let us look at the two sides of this and understand what needs to stay in-house, and what a partner should handle. Information is the life blood of today’s business. The ability […]
Does your IT plan include EDR?

Today’s threats change too quickly for ant-virus products to keep up. By the time a virus is added to the “bad” list on your computer it has changed to something else to avoid detection. This game of cat and mouse is stacked heavily in favor of the cat! All major anti-virus vendors are now shifting […]
When an IT Coordinator makes sense

A mature technology partner and an internal IT Coordinator deliver higher productivity at a lower cost than a fully staffed IT department. Remember the librarian coming to your classroom with the TV cart? It wasn’t that the teacher could not setup and plug in the TV. It was just easier to schedule and have the […]
Are you waiting on your MSP to catch up on security?

Many MSPs are struggling to keep up with the security needs of their customers. The volume of incidents, cost of implementing security solutions, and a reactive approach puts a lot of pressure on them. In the meantime, issues pop up everywhere, further reducing their ability to get a plan together. This often contributes to the […]
Are you hiring for technology roles of the past?

Are you hiring for technology roles of the past? Below are three roles that your business needs to evaluate and consider outsourcing based on today’s technology landscape. This is not an easy process, as there are PEOPLE in these roles that typically have reached the end of their careers or cannot obtain a similarly compensated […]
Do you have a cyber attack response plan?

If your business suffered a (successful) cyber attack today how would you respond? There are no cyber police to call, nor is there a fire department to come put out the flames. A disaster recovery plan is NOT the same as a cyber attack response plan. (CARP) Cyber attacks are happening every second of every […]
Are you in an unhealthy IT relationship?

The IT relationship between business and provider is more important than ever. A healthy relationship generates increased profitability and productivity for both parties. An unhealthy relationship delivers frustration, missed opportunities, and a lack of trust. Most businesses will live with the relationship until a breaking point, usually a ransomware event. The risk of this reactive […]
Workstation recovery is often overlooked in recovery planning

Workstation recovery is the most overlooked part of recovery planning. Recovering all your servers and data without workstations is not useful. This becomes critical as office locations and workstations increase. Reinstalling the operating system and applications for 10 workstations can be brute forced, the same cannot be said for 100. The uncomfortable stares of employees […]
If you think RPO is a football term your business could be in trouble
If you run a business and think RPO means run pass option, your business backup strategy is in trouble. An area of focus we highlighted last week was recovery planning. There are two key concepts in recovery planning. These concepts link directly to the success of your business surviving a ransomware event. It is important […]
Three areas to focus on in the battle against ransomware

The surge in ransomware and cyber attacks is not stopping anytime soon. We have all seen the statistics, but when it is your business the math becomes real. We receive calls on a monthly basis from a business owner that is asking for help recovering from an attack. Unfortunately many of these businesses will not […]
How to perform technology alignment for your growing business

Technology alignment is critical for a growing business, especially as a business scales up. A car that is out of alignment behaves the same as a business. At slow speeds (low growth) the lack of alignment is not noticeable, but once you get on the highway hold on or the car will be drifting across […]
What to watch for when your IT provider is acquired

The IT industry is consolidating at an rapid pace right, especially in the Managed Service Provider (MSP) space. As a buyer we focus on acquisitions that will allow us to provide an enhanced level of services to the Clients and opportunities to the team members we bring on. If you find yourself the Client of […]
3 Blatant Signs Your Technology is in Maintenance Mode

A funny thing happens when some people have success. They quit innovating and get comfortable with the status quo. This same phenomenon happens to businesses all the time especially when it comes to technology. This leads to reduced productivity and profits which no business wants. So how do you know if your technology has entered […]
The job market will force a shift to IT outsourcing for businesses

There is a great corporate migration to Nashville right now. Companies are moving out of the high tax and regulation states like CA and NY and bringing many jobs. This is great for the local economy but will accelerate the need for IT outsourcing for businesses in the area. Business leaders need to plan for […]
A month with a new MacBook Pro versus Surface Laptop

Full disclaimer: I’m a Windows fan and run a successful technology consulting company based on Microsoft products and services. I’m also a user of the majority of products Apple makes, starting with the first iPhone. I bought a new MacBook Pro with the M1 chip and used it as my primary machine for a month […]
When you know it is time to change IT providers

How do you know when it is time to change IT providers? Do you wait until some unforeseen disaster? Until you find out all their best techs have left? Until your competitors are moving past you due to higher levels of tech-enabled productivity? Changing IT providers is right up there with finding a new accounting […]
The bad guys are real and your lack of technology strategy is making it easy for them

The bad guys are real, especially on the Internet. In fact, the bad guys of the Internet are worse than those in real life. At least you can SEE the ones in real life and defend yourself or flee. The baddies of the Internet come into your house, sit on all the furniture, make a […]
Quit trying to “get all the good” out of your computers: Proactive Hardware Lifecycle Management

Business managers continue to want to justify getting all the “good” out of their capital equipment purchases. Computer equipment should no longer be put in this category. Computers on a 4-year hardware lifecycle management will deliver higher productivity for your staff, reduced (or no) downtime, and more overall profit for your business. The computer has […]
Common sense is not so common when it comes to security

The saying, “common sense is not so common” applies to IT security more than we would like to admit. We all have our areas of expertise, but it is now 2021, which means you are participating in IT security whether you like it or not. Here are three common sense ideas you can commit to […]
Quit setting your money on fire

The idea of people actually setting money on fire is pretty humorous. Watching it happen in real life is less satisfying, wasteful even, so let’s stop doing it with our technology spend! A proper technology roadmap will link your spending to business results on an ongoing basis. We have written extensively about this HERE, HERE, […]
Stringfellow Technology Group acquires CTC Networks

Stringfellow Technology Group (“Stringfellow”), based in Nashville, TN, has acquired CTC Networks (“CTC”) based in Franklin, TN. CTC was founded in 1993 and provides managed technology services to the healthcare, manufacturing, and life science industries. All CTC team members joined Stringfellow on November 1st, 2020. CTC president Jim Marable wanted to provide his customers with […]
Email Basics: Securing email with DNS

Do you ever wonder how that email address you type in actually gets delivered? Understanding the basics of email delivery will enhance your understanding of how phishing and spam attacks work. This is a bit technical, but worth understanding as an end-user. For all you technical folks out there this may also be a good […]
Email Basics: Be Secure

Email was not designed with security as a requirement. In fact, all “security” that involves email was bolted on after the fact. Here are four areas that were bolted on that should be part of your secure email basics. Utilize MFA, for real We have beat on this drum for over five years now, and […]
3 Reasons Healthcare Providers Need Security Training

Here are some reasons why it’s important to hire an MSP that offers security awareness training as part of its offering: Reduce the risk of data breaches: Data breaches can be catastrophic for businesses, resulting in loss of data, damage to reputation, and legal liability. Security awareness training can help reduce the risk of […]
Email Basics: Common Sense

Imagine driving without lines on the road, speed limits, or the need to have a license. Now you know what using email for business communication is like…complete and utter chaos. Sure, it’s better than riding a horse to work or sending a telegram, but the value of using email as a communication tool is decreasing […]
M365 Security: Securing devices and applications with Intune
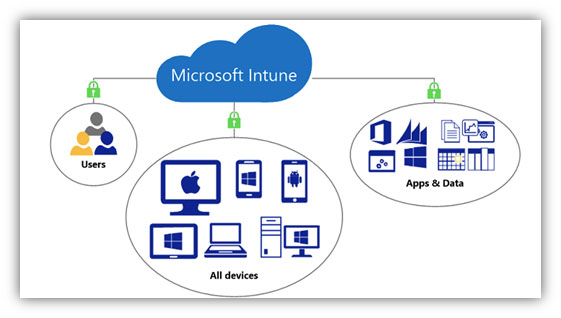
The remote work shift puts the management of devices, applications, and data front and center in the M365 security discussion. The firewall, local Active Directory, and VPN solutions typically don’t scale or consider the vast number of variables when users want to work from any device. Utilizing the features of Microsoft’s Intune services can keep […]
Microsoft 365 Security: Securing email with Advanced Threat Protection

We covered the basic security options that are available to all M365 plans here. This is the equivalent of locking your doors at night, a good idea, but not enough if you have someone that really wants to get into your house. Unfortunately there is no equivalent of a “safe” neighborhood on the Internet, if […]
M365 Security Basics

The question is not whether or not you are using Microsoft 365 (formerly Office 365), but rather, are you using it securely? Microsoft has steadily improved the default security settings, but it still requires some experience to get it 100% there. The amount of attacks on the M365 is astounding, specifically with phishing attempts to […]
Working Remote: Standardize on Teams as your collaboration app

Collaboration is the act of working with someone to produce or create something. In today’s workplace the words “in real time” need to be added to this. Sending emails back and forth is not collaboration, and it is certainly not productive! When working remotely it is critical to standardize on a collaboration application across your […]
Working remote: Time to move on from internal IT support

No matter how good the technology or smart the end-user, there will always be a need for IT support. Plug and Play was a big deal in the 90’s and we all know how that turned out! Getting the most out of your remote workforce requires that you provide IT support that can handle a […]
Working Remote: What hardware setups work best

Sitting at the kitchen table hunched over a laptop screen is not ideal, but it is the situation many are in after the shift to remote work. Based on our experience, the four hardware investments below will increase your productivity and comfort while working remotely. Laptop with decent camera and microphone Most laptops produced in […]