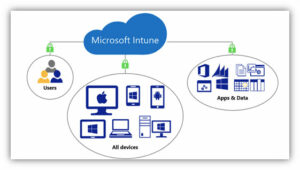
The remote work shift puts the management of devices, applications, and data front and center in the M365 security discussion. The firewall, local Active Directory, and VPN solutions typically don’t scale or consider the vast number of variables when users want to work from any device. Utilizing the features of Microsoft’s Intune services can keep your organization’s data secure while allowing end-users to remain productive wherever they are.
Device management
Microsoft Intune provides the management of ALL devices interacting with your business data, along with the reporting and policies needed to ensure compliance with HIPPA, PHI, and other regulations. We no longer make the distinction between “mobile” devices and computers or personally owned versus corporate-owned devices. The days of carrying a work phone and a personal phone are long gone.
It is critical to understand how to deploy device management for your organization. Being too strict will cause people to “go around” IT to get their work done, not having it configured correctly, and making themselves more susceptible to potential M365 security breaches. Start with a baseline M365 security configuration for ANY device that will have access to corporate resources. Examples of these settings would be to require device encryption, the setting of a PIN code, and a lock screen timeout. These settings are good practices and should be enforced on all devices regardless of type or ownership.
Once the baseline policies are rolled out, consider your organization’s specific protection needs. Can anyone access M365 services from a web browser, or does it need to be from a compliant/managed device? Can users cut/paste corporate data? Store files outside of SharePoint or OneDrive? These questions must be answered to develop policies that can be rolled out to your organization.
Conditional Access
Would you open the door to a stranger without asking their name, intent, or looking through the window? No way! This is the same way Conditional Access works. It evaluates signals when a user or application asks to access corporate resources and makes a decision. The power of this method is that it allows for end-user flexibility without strict enforcement of M365 security policies that often hinder productivity.
Like device management, it is critical to understand how Conditional Access policies will affect your end users BEFORE rolling them out. Determining whether or not we have users outside the US, do we allow data access from web browsers without requiring MFA, or does a device have to comply with all M365 security policies before we allow access? All of these questions need to be addressed prior to rollout.
There is a set of basic Conditional Access policies that should be rolled out to all users, especially with the shift to personal and remote working arrangements. These are actually what the M365 Security Defaults use when enabled, as discussed in our M365 Security Basics post. The issue with this approach is that it does not allow for exceptions or customizations of the policies, which quickly impacts end-user productivity.
Application management and deployment
Securely deploying and managing applications has become a key component of corporate data security. Microsoft Intune has a set of Mobile Application Management (MAM) policies and app protection features to enable this functionality. Like Conditional Access and Device Management, you need to understand how this will impact your users before rolling out.
Controlling the applications and, thus, the data they use is one of the most effective ways to keep your organizational data secure. It also allows for non-corporate managed device access, which is important in remote work scenarios. Deployment of applications to ANY device is also simplified and can be initiated by the end-user without interaction with IT. A win-win if there ever was one!
The Microsoft 365 platform provides advanced controls and policies to keep your end-users productive and secure. Working with an experienced partner to define and deploy these toolsets will ensure a positive experience for end-users and a much higher ROI than “figuring it out” with trial and error. Remember, with great power comes great responsibility!