Imagine driving without lines on the road, speed limits, or the need to have a license. Now you know what using email for business communication is like…complete and utter chaos. Sure, it’s better than riding a horse to work or sending a telegram, but the value of using email as a communication tool is decreasing daily. In a previous post we covered how to stop using email, and these email basics are now more important than ever.
Do not forward or reply…delete
Do not forward your spam, suspicious, suspect, strange, or weird email to anyone, especially the helpdesk! If you have to do that, guess what, you are now part of the problem. Also, don’t reply to the person sending the email as this also makes the problem worse. It is trivial to fake the FROM address of an email just like you could with a mailed paper letter. If you have to question is this legit or not, then it is not….simple.
We are conditioned to want to be needed and wanted, so our first impulse is to NEED that email to be important. This is exactly how the scams work! Of course, the CFO “needs” you to provide her with the latest finances, or the head of HR has asked you about a “special project”. Nope, they do not need your help, and if they did it would be requested via a call, not a random email. Use common sense, delete the email and move on with your day. If it was indeed important it will show up as a call or office visit in the near future!
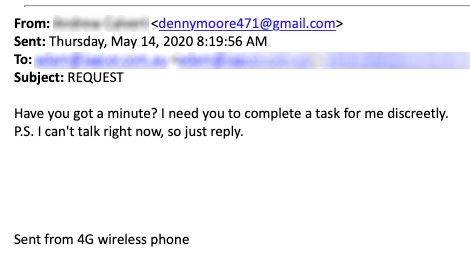
Example of phishing email request from boss:
Do not log in via the link
This is the number one way to have your accounts compromised. An email shows up with a link to an important file, invoice, report, or document. It looks like it is from OneDrive, Dropbox, or any number of programs you use all the time. First, ask yourself am I expecting this? Likely not, but it is crafted to *really* make you want to click. So you do…
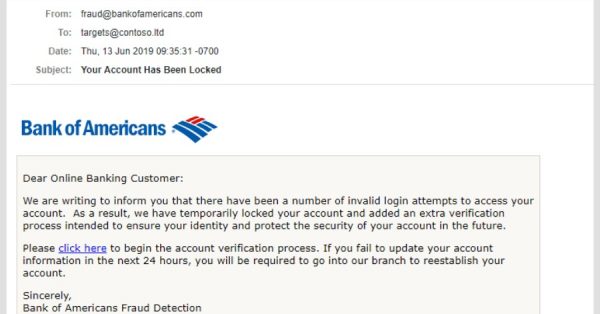
Example of phishing email from bank…note the spelling in the from address:
The login site will look identical to the normal login screen you are used to. You will login with your username and password, and then it is done. Your credentials are now in the hands of a hacker and they are downloading all your information (or at least reading it) seconds later. MFA will stop 99% of these attacks, but many users do not have this setup for all their services.
If you must login to a service, do so from a new web browser window, or local application, that you know is secure. Do not use the link from the random email. Yes, sometimes the link is unique to you and must be used, but even then ask yourself, was this expected?
No one will ask for your password via email, ever…
Email should be considered completely secure and never used to transmit sensitive information without encryption services turned on. Knowing that why would Microsoft, Apple, or your bank ever ask you for your password this way? They would not, nor would they call you on the phone to let you know your account was compromised!
Any support provider should be able to assist you without the knowledge of your password, or at a minimum, they can work with you to input the password via screen share (not perfect), and then you can reset it later. Again MFA will solve all of this as you will maintain control of the account via your security token (mobile phone), so set that up whenever possible.
Following these simple rules of the road will keep you and everyone else around you safer and more productive. Remember, there is no shame in deleting an email!

