6 Proven strategies to keep your work devices secure

The rise of remote work and virtual communication has made it more important than ever to secure our devices against cyberthreats. Hackers are constantly finding new ways to exploit our digital vulnerabilities, from webcam spying to unauthorized screen viewing. But don’t worry! There are steps you can take to protect yourself. Install anti-malware software No […]
Improve internet security with VPN

Even if you’re using a firewall and anti-malware software, hackers could still intercept data being sent to and from your device. So if you’re not using a virtual private network (VPN) to browse the internet, you’re leaving your business at risk of data theft. What is a VPN? A VPN creates an encrypted tunnel between […]
Watering hole attack: What it is and how to protect against it

Watering hole attacks have become more common in recent years and pose a serious threat to organizations everywhere. Read on to learn more about what watering hole attacks and how your business can stay one step ahead of cybercriminals. How watering hole attacks work The term “watering hole” colloquially refers to a social gathering place […]
Work from home security best practices

In many industries, remote working is becoming an increasingly popular option for employees. But with the freedom and flexibility of working from home comes a new set of cybersecurity risks. Read on to learn security best practices for remote workers. Patch your software regularly Although installing software updates can be a major nuisance, these updates […]
Surf securely with a VPN

There was a time when installing an antivirus program was enough to secure your data, but that’s no longer the case today. Whether you want to keep your online activities hidden from third parties or prevent your data from being intercepted by hackers, you need to invest in a virtual private network (VPN). What is […]
Don’t be a victim of watering hole attacks

With cybercriminals continuously developing new ways to infiltrate networks and steal user data, it is more crucial than ever to stay one step ahead of these perpetrators. Protect yourself from one of the most common methods that cybercriminals use to inject malware into computers: watering hole attacks. The term “watering hole” colloquially refers to a […]
M365 Security: Securing devices and applications with Intune
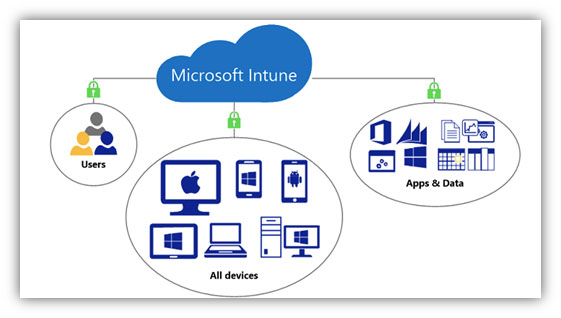
The remote work shift puts the management of devices, applications, and data front and center in the M365 security discussion. The firewall, local Active Directory, and VPN solutions typically don’t scale or consider the vast number of variables when users want to work from any device. Utilizing the features of Microsoft’s Intune services can keep […]
Working remote: Time to move on from internal IT support

No matter how good the technology or smart the end-user, there will always be a need for IT support. Plug and Play was a big deal in the 90’s and we all know how that turned out! Getting the most out of your remote workforce requires that you provide IT support that can handle a […]
How to pick a VPN for your business

A virtual private network (VPN) offers a host of security and privacy benefits, especially if you’re surfing the web or transacting online over a public Wi-Fi network. A VPN ensures that your online activities are always secure and private. So what factors do you need to consider when selecting a VPN, and how do you […]
From Servers to Services: The Great Purge

What is the first thing that happens before you move homes? All of those old clothes, exercise equipment, and children’s toys go off to the donation bin. This is also known as The Great Purge. The analog nature of all this stuff means that you are going to put it in boxes to haul it […]
From Servers to Services: A great game of technology Jenga

Going from servers to services is a lot like playing a game of Jenga. You have to pull out all the various blocks (apps) without knocking over the tower (your business). You can go for the slow methodical method, or the “turn if off and see who complains” method. We have found a balance between […]
5 Ways to optimize your new laptop

So you’ve just unboxed your brand new laptop — what do you do next? Before you start using it to surf the internet or finish your tasks for the day, take these steps to optimize its performance and ensure it meets your needs. 1. Update your laptop’s operating system One of the first things you […]
Recalibrate your technology plan: Cloud Collaboration
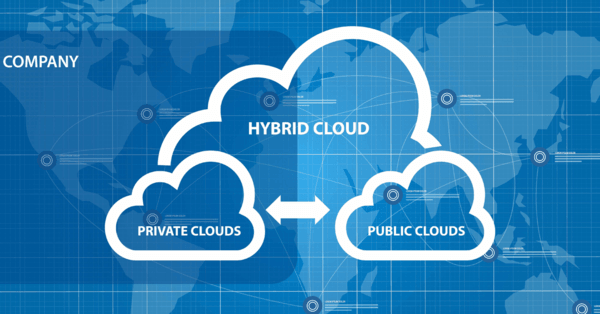
Workforce collaboration has changed. We aren’t going back to conference rooms full of people, and that’s a good thing. When you are recalibrating your technology plan, enabling cloud collaboration should be a part of it. This is more than video conferencing and screen sharing. Cloud collaboration is accessing information and collaborating in an ad-hoc, yet […]
Recalibrate your technology plan: Zero Trust Security
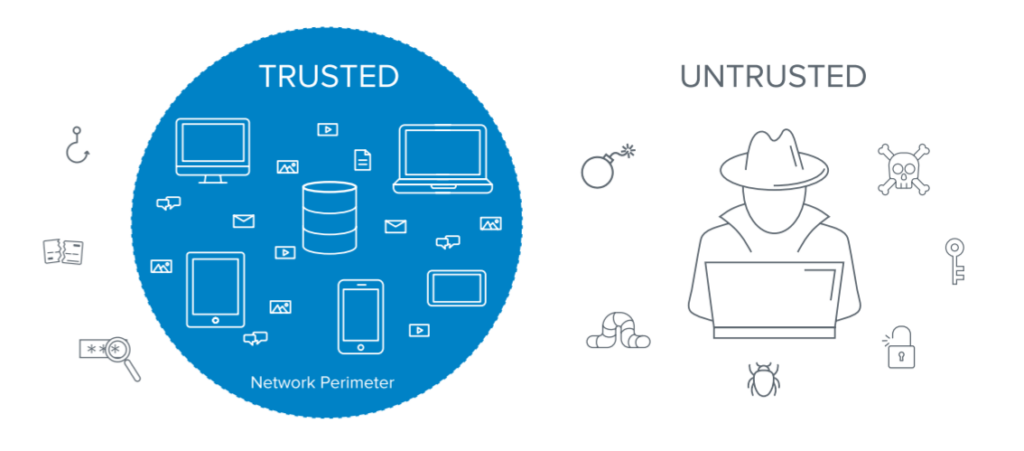
Get ready to hear much about the Zero Trust security model in the future. The #wfh movement has put this front and center in any technology planning discussion. This is not a fad or product to implement, it’s a mindset shift that needs to occur in our technology planning. Many security models were built on […]
Security best practices for remote workers

Working from home increases employee autonomy, cuts costs, and ensures the health and safety of the company during the coronavirus pandemic. The problem is, it also increases the likelihood of security breaches since employees are working outside the company’s security perimeter. That’s why you and your staff must adhere to these security best practices. Fortify […]
Tips and tricks to prevent watering hole attacks

Hackers are getting creative nowadays with their illicit activities, which means the onus is on computer users to take steps to protect their computers. The first step to staying ahead of the game is by learning more about cyberattacks. Here are some pointers to help you deal with oneway criminals steal data: watering hole attacks. […]
Enjoy an improved laptop experience

Laptops may not be the most powerful computers, but the benefits they provide are undisputable. For one thing, they deliver a similar user experience as your huge desktop PC, but much more conveniently and affordably. But before you reap their many benefits, here are five steps you should take before using them to improve their […]
Why you need a VPN and how to choose one

Installing antivirus software and setting strong passwords are no longer considered the bare minimum in cybersecurity. With hackers, third parties, and ISPs constantly monitoring networks and your online habits, hopping onto a virtual private network (VPN) is crucial for keeping your surfing habits private. Here’s why. What is a VPN? The best way to describe […]
What are watering hole attacks?

Hackers have plenty of ways to breach your systems. They can use complex programs to exploit software bugs, send emails to dupe you into downloading malware, or insert a malware-infected USB drive directly into your computer. However, another increasingly popular hacking method is a watering hole attack. What are watering hole attacks? Much like phishing, […]
Enhance your new laptop in 5 steps

Getting a new laptop can be very exciting. It guarantees a more seamless user experience with faster speed, more memory, and better battery life. But it’s all for naught if you don’t take certain preventive steps before using your new machine. Discover five things you should do before you start exploring your new toy. 1. […]
VPNs: Why you need them
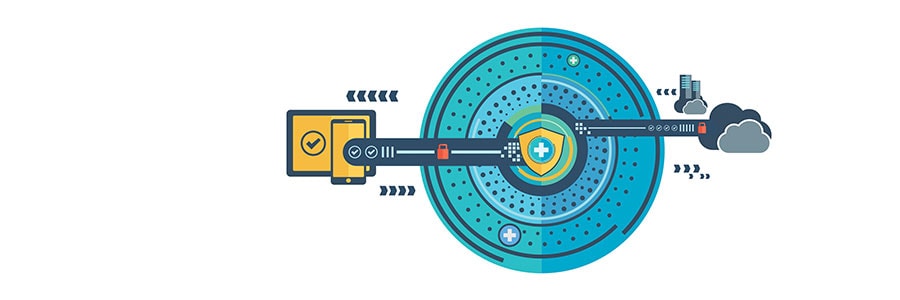
Whether it’s because of government surveillance or cyberattacks, internet users are more concerned than ever about the privacy of their online activities. Unfortunately, security measures like firewalls and antivirus software can’t help you in this case, but there’s one that can: Virtual Private Network (VPN). What is VPN? Simply put, a VPN is a group […]
Hackers KRACK WiFi security

You’ve heard of ransomware, denial-of-service attacks, and even phishing, but one hacking technique you may not have heard of is the KRACK exploit. This attack takes advantage of a vulnerability in WiFi networks, which puts any device with a wireless connection at risk. Here’s everything you need to know about KRACK. What is KRACK? Simply […]
Virtualize your network with telecom giants

With virtualization yet to make its way into the lexicon of common tech phrases, many business owners are still trying to decipher the full extent of its value. Various aspects of the service have evolved over time, and we can probably expect more to come. For now, however, one of its existing functions is getting […]