Get ready to hear much about the Zero Trust security model in the future. The #wfh movement has put this front and center in any technology planning discussion. This is not a fad or product to implement, it’s a mindset shift that needs to occur in our technology planning.
Many security models were built on putting all your important digital assets on the corporate network and then building walls around it. All the devices physically on the network could access the data, but only after they authenticated with a username and password. We all know how this ends. As we’ve outlined here, passwords are eventually proven useless as a security measure for companies, and network boundaries are blurred and broken once users work outside their offices.
Users expect to get on any Wifi connection and then have access to corporate data. This means we have to plan for insecure public networks to be the norm while also acknowledging that VPN technology is not flexible or scalable enough to be a solution to this anymore.
The formal NIST model will be released in the near future, but for now, let’s review two key areas of the Zero Trust model that you need to plan for.
Never Trust, Always Verify
Strong identity and access management controls are the key to the Zero Trust model. The ability to positively verify and secure your user’s identities (logins) must be a capability in your technology planning for the future. Microsoft has embraced this model, and baked it into the new Microsoft 365 service offerings. The caveat is that you have to understand how to enable and manage these controls.
Microsoft Azure Active Directory should be your central hub for all identity management and verification. You should utilize this for Single Sign On (SSO) services for your applications whenever possible. Conditional Access provides powerful controls to enable the zero-trust model as well. Properly configured, Conditional Access can make real-time decisions on user access requests that will ensure the user, device, and resource are all protected.
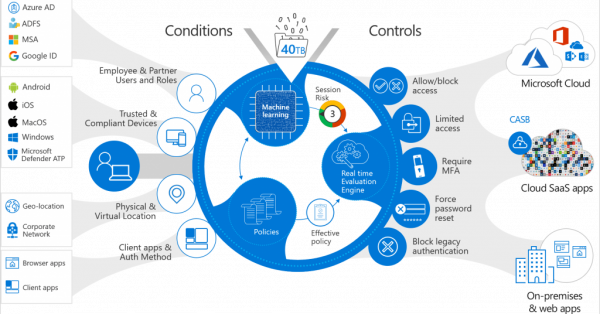
Deploy device management policies
The old model was to issue “corporate” laptops that had various restrictions and software placed on them to ensure security. If you weren’t at the office, you had to connect to the VPN to obtain access. All of this is very cumbersome for the user and, in the end, not that secure. Then came mobile devices and coffee shops!
Users wanted access to corporate resources on their personal devices (BYOD) and usually on a non-trusted (coffee shop) network. The way to make this happen is to have the ability to validate that the device is in a secure state before allowing access. This can be accomplished in various ways, and one of the best is if you are using Microsoft 365 to set up and utilize Intune.
Intune allows you to develop policies for all devices attempting to access corporate or personal corporate resources. This allows maximum user flexibility while keeping your data and applications secure. It is also fully integrated with Azure Active Directory, and Conditional Access controls for a seamless user experience.