Don’t let ransomware ruin your Mac

If you’re a Mac user, it’s important to be aware of the growing number of ransomware attacks that are specifically targeting macOS devices. Just like Windows users, you need to take precautions to protect yourself from these threats. Here’s how you can secure your Mac against ransomware attacks. Defining ransomware Ransomware is a type of […]
It starts with a notification…

A notification in your pocket dings and lets you know someone is trying to log into your email. That’s weird, you think, I didn’t do that. Upon closer inspection, you notice the login request is coming from Paris, France. Something’s not right. A hacker phished You. The excel spreadsheet that your work colleague sent you […]
How to Protect Yourself from Internet Hoaxes 101

Cybersecurity is a fast-changing, stressful, and downright scary space to play in. The number and sophistication of cyberattacks are on the rise as hackers continue to outsmart preventive security measures and seep into our environments. It’s becoming evident that navigating how to protect yourself from internet hoaxes and cyber crimes is more challenging than it […]
How Microsoft 365 Defender is helping fight phishing

If you’re looking for comprehensive protection against phishing and other online threats, you can’t go wrong with Microsoft 365 Defender. Read on to learn about Microsoft 365 Defender’s powerful cybersecurity features and its myriad benefits to businesses like yours. Phishing is one of the most common methods used by cybercriminals to steal sensitive information such […]
Email account security you should follow

Your email account is one of the most important pieces of online property you own. It’s the gateway to your other online accounts. If your email account falls into the wrong hands, it can be used to wreak havoc on your business. Here are surefire ways to bolster your email account security. Use strong passwords […]
A guide to IT security terms everyone should know

You’ve probably heard the term “malware” thrown around a lot, but what does it actually mean? In this article, we will define malware and a few other commonly used terms in IT so you can better protect your business. Understanding these basic cybersecurity concepts doesn’t require deep IT expertise, so read on. Malware For a […]
Protecting your Microsoft 365 environment and data

For many businesses, Microsoft 365 is their go-to productivity suite because it offers powerful features, cost-saving benefits, and world-class security. And while Microsoft continuously looks for ways to address security concerns, the changing threat landscape can put Microsoft 365’s security measures to the test. Here are some of the most common security risks Microsoft 365 […]
Work from home security best practices

In many industries, remote working is becoming an increasingly popular option for employees. But with the freedom and flexibility of working from home comes a new set of cybersecurity risks. Read on to learn security best practices for remote workers. Patch your software regularly Although installing software updates can be a major nuisance, these updates […]
The crucial role of MSPs in SMB cybersecurity

With modern cyberattacks targeting companies of all sizes, businesses cannot afford to relegate cybersecurity to the bottom of their list of priorities. When it comes to cybersecurity, even small- and mid-sized businesses (SMBs) would do well to get help from an expert. Here’s how having a managed IT services provider (MSP) implement robust cybersecurity solutions […]
What you need to know about Mac ransomware

New strains of ransomware usually impact many Windows users, while only a small percentage of Mac users get affected. However, there are ransomware strains that specifically target Apple computers. Boost your defenses against these threats by following these security tips. What is ransomware? Ransomware is a type of malicious software that holds computer systems hostage […]
Prevent phishing attacks with these Microsoft 365 Defender features

Microsoft is a provider of powerful and intuitive tools that improve efficiency, productivity, and security. And as phishing attacks become more sophisticated and prevalent, Microsoft is taking steps to protect its users, one of which is releasing powerful cybersecurity tools via Microsoft 365 Defender. Here are some of them. 1. Anti-phishing The most dangerous types […]
Helpful tips for keeping your email safe

People rely on email to do a wide array of tasks. We use it to sign up for websites, apply for jobs, make payments, get in touch with friends and family, and many more. However, email is also commonly exploited by hackers to steal information or launch malware attacks. Here are crucial steps to take […]
Basic cybersecurity terms everyone should know

If the only cybersecurity terms you know are “virus” and “hacking,” now is the time to expand your cybersecurity vocabulary. This will enable you to better understand the variety of risks in the online world and protect your computers, data, and yourself. Here’s a short yet handy list of cybersecurity terms you should know. Malware […]
Simple ways to defend against Mac ransomware

Although a majority of ransomware attacks usually target Windows PCs, this doesn’t mean Mac users are completely safe. Ransomware attacks for Macs have occurred before, and are growing more widespread over time. So how can you prevent ransomware from infecting your Mac? We’ve compiled some helpful security tips for you. What is Mac ransomware? Ransomware […]
Email Basics: Securing email with DNS

Do you ever wonder how that email address you type in actually gets delivered? Understanding the basics of email delivery will enhance your understanding of how phishing and spam attacks work. This is a bit technical, but worth understanding as an end-user. For all you technical folks out there this may also be a good […]
Email Basics: Common Sense

Imagine driving without lines on the road, speed limits, or the need to have a license. Now you know what using email for business communication is like…complete and utter chaos. Sure, it’s better than riding a horse to work or sending a telegram, but the value of using email as a communication tool is decreasing […]
Small- and mid-sized businesses need cybersecurity

If your company has recently suffered from a data breach or a ransomware attack, then you know how costly it can be. You lose not just hundreds of dollars but also the reputation you’ve built through the years. That’s why you need cutting-edge cybersecurity solutions to protect your business from ever-growing cybersecurity threats. The good […]
Fighting phishing scams with Microsoft 365

Microsoft is a known provider of top-tier business productivity software — and its commitment to its subscribers’ cybersecurity is integral to that reputation. To fight phishing, one of today’s most prevalent cyberthreats, the tech titan has equipped Microsoft 365 with powerful features. Among the many business solutions that Microsoft offers is email hosting through Outlook. […]
How you keep your email account safe

Everyone uses email to send and receive sensitive information, making it an attractive target for cyberattacks. The importance of email security is vital to your company’s operations, so applying the following tips can dramatically reduce your exposure to hackers and malware. Use separate email accounts Most people use a single email account for all their […]
Security best practices for remote workers

Working from home increases employee autonomy, cuts costs, and ensures the health and safety of the company during the coronavirus pandemic. The problem is, it also increases the likelihood of security breaches since employees are working outside the company’s security perimeter. That’s why you and your staff must adhere to these security best practices. Fortify […]
Mac security 101: Ransomware

Whenever a new strain of ransomware is discovered, Mac users are barely affected by the news. But there are rare occasions where ransomware specifically targets Mac computers. Being aware of and knowing how to defend against these threats is crucial if your business mostly relies on Mac devices. Here’s what you need to know about […]
Gmail’s proactive anti-phishing enhancements

To this day, cybercriminals still have an old reliable weapon in their arsenal — email. With it, criminals can fool recipients into revealing personal information or clicking on a malware-ridden attachment. This kind of scam is called phishing, and it continues to persist because many people still fall for it. To protect email users from […]
5 Tips for securing your email account

Email is one of the best things the internet has made possible. We use email to signup for websites, apply for jobs, make payments, and many more. But email users also run the risk of account hijacking, malware attacks, and other cyberthreats. To secure your emails, follow these crucial tips. Use separate email accounts Most […]
Get ahead of cybersecurity with these basic IT terms

Cybersecurity is everyone’s responsibility. But you don’t need to be an IT expert to know how to protect yourself from a cyberattack. To help you get started, here are helpful terms you need to know so you’re not left in the dark, whether you’re teaching yourself how to update your anti-malware, updating your systems, or […]
How to protect your iPhone from phishers

Phishing scams have been around for years, and they’ve gotten smarter with time. Recently, criminals have been targeting iPhone users through a voice phishing scam that makes the call appear like it’s coming from Apple Support. Fortunately, there are simple but effective tips so you don’t fall prey to this notorious scheme. If you receive […]
How Office 365 deals with phishing attacks

There are plenty of things to love about Office 365. For a small monthly fee, it gives you the latest cloud-based version of Microsoft Office apps and robust communication tools that improve collaboration and productivity. But it’s also an extremely secure platform that can defend against the most cunning phishing attacks. Effective anti-phishing solutions must […]
Beware of these social engineering tactics

The volume of malicious cyber attacks is increasing every year. Although many companies use the latest network security systems, they aren’t immune to the hackers’ favorite strategy — social engineering. Unlike malware, social engineering tricks people into volunteering sensitive data. Here’s what you should know to protect your business. Phishing This is the most frequently […]
PhishPoint attack looks like SharePoint

Phishing scams disguise malicious links and emails as messages from trusted sources. The most recent scam to watch out for almost perfectly imitates a trusted invitation to collaborate through Microsoft SharePoint. It’s a three-step attack that’s easy to avoid if you know how it works. Step 1 – Invitation to collaborate email The first thing […]
Gearing up for phishing scams in tax season

As tax season looms, so do phishing scams. For cybercriminals, this is the ideal time of year to deceive unsuspecting individuals into releasing sensitive private or company information. Businesses must therefore take extra precautions between now and April 17th to avoid hackers from selling your confidential data in the dark web. Phishing baits to watch […]
Google releases year-long security study

Passwords are your first line of defense against hackers. But over the years, they have developed plenty of methods to steal them. To gain a deeper understanding of how cybercriminals operate, Google analyzed the causes of leaked login credentials. Here are the results. The results From March 2016 to March 2017, Google and UC Berkeley […]
Beware the Mac malware stealing bank info

In yet another sign that Apple computers are no longer being ignored by hackers, a successful piece of Windows-based malware has been rewritten for MacOS. Instead of encrypting data and holding it for ransom, OSX.Dok skips the extortion and simply steals your bank account information. Read on to learn what you can do to prevent […]
New anti-phishing features for Gmail

Cybercriminals have been relentless throughout 2017. In the past couple of months, hackers discovered new malware strains and software vulnerabilities that have overwhelmed thousands of businesses worldwide. But despite these new attacks, hackers still have an old, yet effective trick up their sleeves: phishing scams. To this day, sending fraudulent emails to steal sensitive information […]
Lessons learned from the WannaCry malware

No one can escape the news of WannaCry. The IT industry has been covering this type of malware for years, but never has one campaign spread so far or infected so many computers. Read on to gain a greater understanding of what happened and how to prepare yourself for the inevitable copy cats. Ransomware review […]
This fake Google app is really a phishing scam
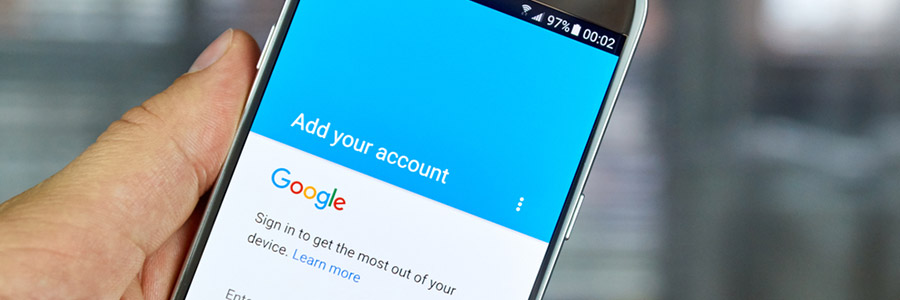
As the technology that recognizes and thwarts malware becomes more advanced, hackers are finding it much easier to trick overly trusting humans to do their dirty work for them. Known as social engineering, it’s a dangerous trend that is becoming increasingly prevalent. Read on to educate yourself on how to avoid the most recent scam […]
Why you need to update Microsoft Word

Software developers and hackers are in a constant game of cat and mouse. When cybercriminals find new security bugs to exploit, tech companies have to quickly release a solution that secures those vulnerabilities. Just this month, Microsoft released a patch to eliminate a Word exploit designed to steal user information. If you’re an avid Microsoft […]
Sly phishing attack catching users off guard

Most phishing attacks involve hiding malicious hyperlinks hidden behind enticing ad images or false-front URLs. Whatever the strategy is, phishing almost always relies on users clicking a link before checking where it really leads. But even the most cautious users may get caught up in the most recent scam. Take a look at our advice […]
Cyber-crime and social engineering

Social engineering is the ability to manipulate people into willfully giving up their confidential information. The data varies, but in terms of cyber security this usually means passwords and bank information. Criminals are using social engineering to gain access to your business and its network by exploiting employees who often don’t have a clue about […]
9 cybersecurity terms everyone must know

As with all technology, trendy phrases come and go with the passing of every IT conference and newly released virus. And when dealing with cybersecurity, keeping up with them all can mean the survival — or demise — of a business. If you’re looking for a list of the industry’s most relevant terms, you’ve come […]
Don’t let hackers fool you with these tricks

Every time we learn about a cyberattack that has affected so many businesses, we invest in security technologies that will safeguard our systems. This year, however, social engineering attacks have taken center stage in the Rio Olympics. Using various scams, hackers can circumvent network security systems by convincing gullible users into giving away sensitive information. […]