M365 Security: Securing devices and applications with Intune
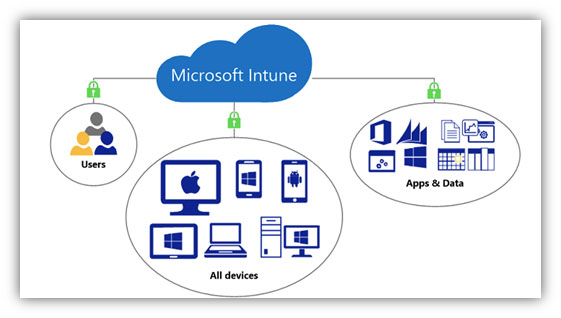
The remote work shift puts the management of devices, applications, and data front and center in the M365 security discussion. The firewall, local Active Directory, and VPN solutions typically don’t scale or consider the vast number of variables when users want to work from any device. Utilizing the features of Microsoft’s Intune services can keep […]
M365 Security Basics

The question is not whether or not you are using Microsoft 365 (formerly Office 365), but rather, are you using it securely? Microsoft has steadily improved the default security settings, but it still requires some experience to get it 100% there. The amount of attacks on the M365 is astounding, specifically with phishing attempts to […]
From Servers to Services: Moving Day

You have made a list and checked it twice, and figured out what apps are naughty and nice. Now it is time to actually make the move from Servers to Services. The key to this final step is a well thought out migration (and fallback) plan. A clean install is best Unless you cannot re-install […]
From Servers to Services: The Great Purge

What is the first thing that happens before you move homes? All of those old clothes, exercise equipment, and children’s toys go off to the donation bin. This is also known as The Great Purge. The analog nature of all this stuff means that you are going to put it in boxes to haul it […]
From Servers to Services: A great game of technology Jenga

Going from servers to services is a lot like playing a game of Jenga. You have to pull out all the various blocks (apps) without knocking over the tower (your business). You can go for the slow methodical method, or the “turn if off and see who complains” method. We have found a balance between […]
New Edge browser better than Chrome for Microsoft 365 users

The new Microsoft Edge browser has finally caught up to Google’s Chrome browser, and the timing is great. The #wfh transition means that more personal devices are being utilized to access corporate resources. Often this is done via a web browser, which means your corporate security could depend on what browser they are using! Microsoft […]
Recalibrate your technology plan: Zero Trust Security
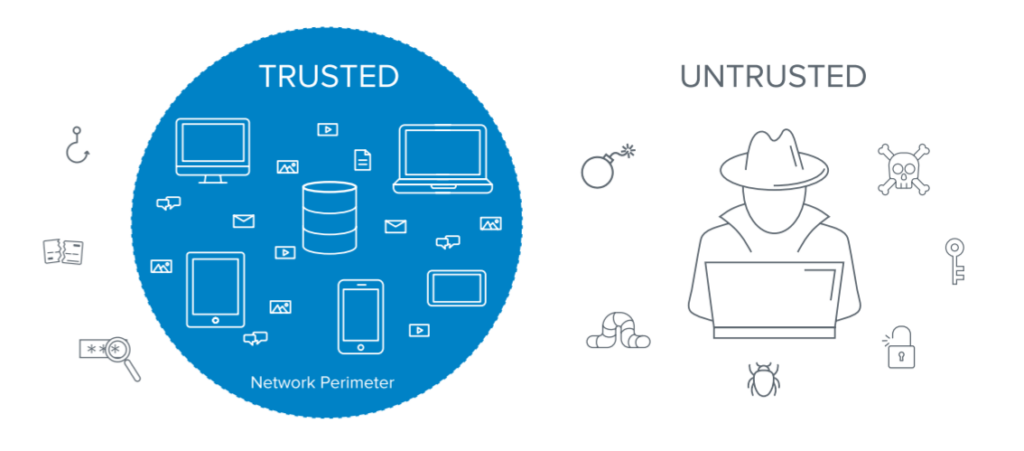
Get ready to hear much about the Zero Trust security model in the future. The #wfh movement has put this front and center in any technology planning discussion. This is not a fad or product to implement, it’s a mindset shift that needs to occur in our technology planning. Many security models were built on […]