The Importance of MFA in Healthcare
In recognition of Cybersecurity Awareness Month, it’s opportunity to delve into a pivotal element of our cybersecurity blueprint—Multi-Factor Authentication (MFA). Understanding Multi-Factor Authentication (MFA): MFA fortifies our defense mechanism by granting access solely upon the successful validation through two or more distinct verification avenues, such as: · Knowledge-Based Verification: Typically, a password or PIN. · […]
MFA is like green beans, you just gotta eat them!

MFA is no longer optional in today’s threat landscape. Over three YEARS ago we started talking to our Clients about utilizing MFA, as passwords are no longer keeping your information safe. The number of IT providers that STILL do not ENFORCE this critical security configuration is very surprising. No one likes to be told what […]
Keep Your Clinics Safer with Stringfellow and Microsoft 365 – October 2023 Webinar

This month’s live webinar, “Keep Your Clinics Safer with Stringfellow and Microsoft 365,” was a success! Daniel Lenerville and Edward Stringfellow discussed cybersecurity and the latest HHS guidelines for healthcare groups. Welcome to Daniel on his first appearance on the webinar, I am delighted to have him on the show and at the company. His […]
April 2023 Webinar: Zero Trust and Why It Matters
April 2023 Webinar: Zero Trust and Why It Matters from Edward Stringfellow on Vimeo. Transcript below Daniel Buchanan: Hello and welcome to the Stringfellow April 2023 webinar and podcast. Our topic this month is Zero Trust and Why It Matters, protecting Patient Data and Enhancing Security. I’m joined again with Edward Stringfellow today. Say, hi, […]
How to ensure the security of IoT devices in healthcare

With the widespread implementation of the Internet of Things (IoT) in healthcare, security concerns that were previously not considered have suddenly become a reality. In 2022, attacks using malware increased by 38% compared to the previous year. This equates to 1410 attacks per week – something device vendors must pay close attention to. Here are […]
6 Proven strategies to keep your work devices secure

The rise of remote work and virtual communication has made it more important than ever to secure our devices against cyberthreats. Hackers are constantly finding new ways to exploit our digital vulnerabilities, from webcam spying to unauthorized screen viewing. But don’t worry! There are steps you can take to protect yourself. Install anti-malware software No […]
Don’t let ransomware ruin your Mac

If you’re a Mac user, it’s important to be aware of the growing number of ransomware attacks that are specifically targeting macOS devices. Just like Windows users, you need to take precautions to protect yourself from these threats. Here’s how you can secure your Mac against ransomware attacks. Defining ransomware Ransomware is a type of […]
The crucial role of identity and access management in cybersecurity

When it comes to protecting your business from cyberattacks, you can never be too careful. Hackers are always looking for any opportunity to steal critical data or wreak havoc on company systems. To truly secure your business from cyberattacks, you need a comprehensive identity and access management (IAM) solution. IAM: An overview IAM is a […]
It starts with a notification…

A notification in your pocket dings and lets you know someone is trying to log into your email. That’s weird, you think, I didn’t do that. Upon closer inspection, you notice the login request is coming from Paris, France. Something’s not right. A hacker phished You. The excel spreadsheet that your work colleague sent you […]
Beware of hackers this holiday season: Tips to protect yourself

With the holidays just around the corner, now is the time for your business to start preparing for potential cyberattacks. Hackers are well aware that during this season, business owners are preoccupied and may let their guard down, so take extra precautions and follow these tips. Change passwords frequently Change your business passwords every three […]
How to create stronger passwords

Passwords are a necessary evil in today’s world. We need them to protect our online identities, but they can be a pain to remember and type in. That’s why it’s important to ensure your passwords are up to date and compliant with the National Institute of Standards and Technology (NIST) guidelines. NIST released updated password […]
Email account security you should follow

Your email account is one of the most important pieces of online property you own. It’s the gateway to your other online accounts. If your email account falls into the wrong hands, it can be used to wreak havoc on your business. Here are surefire ways to bolster your email account security. Use strong passwords […]
A guide to protecting your Microsoft 365 data

Microsoft 365 offers a number of features to help you protect your business’s data. In this article, we provide seven ways to boost data protection in Microsoft 365. Follow these tips so you can rest assured that your data is safe and secure. Secure mobile devices It’s common for employees nowadays to use personal smartphones […]
How to improve your online security: Tips for safe surfing

For many, the internet is an important part of their everyday lives. They use it for shopping, banking, and keeping in touch with loved ones and friends. A lot of people, however, are not aware of the many cyberthreats that can steal sensitive information or corrupt their data. In this article, we will discuss how […]
Securing Microsoft Teams: Practical tips to keep your workplace safe

Microsoft Teams is a great tool that can help improve communication and collaboration in the workplace. However, the popular business communication platform can also be a security concern if it’s not adequately secured. In this blog, we’ll dive into some practical tips for securing Microsoft Teams and keeping your workplace safe. Utilize built-in security features […]
Work from home security best practices

In many industries, remote working is becoming an increasingly popular option for employees. But with the freedom and flexibility of working from home comes a new set of cybersecurity risks. Read on to learn security best practices for remote workers. Patch your software regularly Although installing software updates can be a major nuisance, these updates […]
Are you waiting on your MSP to catch up on security?

Many MSPs are struggling to keep up with the security needs of their customers. The volume of incidents, cost of implementing security solutions, and a reactive approach puts a lot of pressure on them. In the meantime, issues pop up everywhere, further reducing their ability to get a plan together. This often contributes to the […]
The benefits of identity and access management to your organization

Every technology you use — whether it’s a cloud-based program, a mobile application, or on-premises servers — contains sensitive business data vital to conducting operations. So how can you ensure the security of such data from cyberthreats like identity theft, phishing attacks, and other forms of fraud? Identity and access management (IAM) is the answer […]
Your password may not be secure — update it now
The National Institute of Standards and Technology (NIST) once said that a good password consisted of three things: upper- and lowercase letters, numbers, and symbols. However, the NIST has now reversed its stance on good passwords. Here’s why and what they are now recommending. The problem The issue isn’t that the NIST advised people to […]
Microsoft 365 data loss protection: A quick and easy guide

Businesses of all sizes and across all sectors are turning to Microsoft 365 for the productivity-boosting benefits it offers. Many also choose the subscription service for its robust security features designed to safeguard against cyberthreats of all kinds. To make the most out of these functionalities and ensure your business data’s security, follow these tips. […]
3 Simple tips for thwarting cybercriminals

Advances in technology have made life easier but have also enabled cybercriminals to improve their techniques. This can be a big blow to small-business owners who often take data security for granted. To keep your business safe, follow these simple tips. Cover your webcam If Facebook founder Mark Zuckerberg, former FBI Director James Comey, and […]
Common sense is not so common when it comes to security

The saying, “common sense is not so common” applies to IT security more than we would like to admit. We all have our areas of expertise, but it is now 2021, which means you are participating in IT security whether you like it or not. Here are three common sense ideas you can commit to […]
Improve internet security with these easy tips

With over four billion internet users around the globe totaling roughly 59% of the population, the internet is rife with opportunities for hackers to steal users’ information. And with technology constantly evolving and the internet growing, it’s not likely to get safer anytime soon. It therefore pays to take extra precautions when surfing the web. […]
Email Basics: Be Secure

Email was not designed with security as a requirement. In fact, all “security” that involves email was bolted on after the fact. Here are four areas that were bolted on that should be part of your secure email basics. Utilize MFA, for real We have beat on this drum for over five years now, and […]
Email Basics: Common Sense

Imagine driving without lines on the road, speed limits, or the need to have a license. Now you know what using email for business communication is like…complete and utter chaos. Sure, it’s better than riding a horse to work or sending a telegram, but the value of using email as a communication tool is decreasing […]
M365 Security: Securing devices and applications with Intune
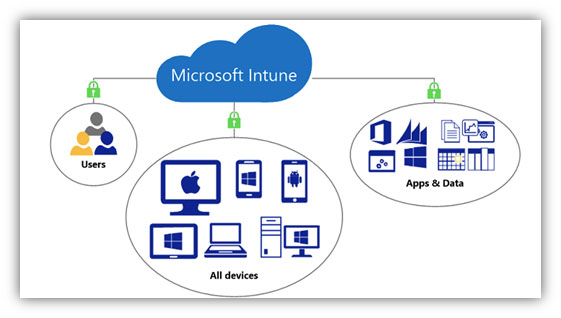
The remote work shift puts the management of devices, applications, and data front and center in the M365 security discussion. The firewall, local Active Directory, and VPN solutions typically don’t scale or consider the vast number of variables when users want to work from any device. Utilizing the features of Microsoft’s Intune services can keep […]
M365 Security Basics

The question is not whether or not you are using Microsoft 365 (formerly Office 365), but rather, are you using it securely? Microsoft has steadily improved the default security settings, but it still requires some experience to get it 100% there. The amount of attacks on the M365 is astounding, specifically with phishing attempts to […]
How you keep your email account safe

Everyone uses email to send and receive sensitive information, making it an attractive target for cyberattacks. The importance of email security is vital to your company’s operations, so applying the following tips can dramatically reduce your exposure to hackers and malware. Use separate email accounts Most people use a single email account for all their […]
It is time to recalibrate your technology plan

No matter how good your technology plan was going into 2020, it is time to recalibrate it. The business environment has permanently changed and will not be going back to “how it was” with or without COVID-19. Thousands of workers shifted to #wfh for the first time, and guess what? They were MORE productive than […]
Security best practices for remote workers

Working from home increases employee autonomy, cuts costs, and ensures the health and safety of the company during the coronavirus pandemic. The problem is, it also increases the likelihood of security breaches since employees are working outside the company’s security perimeter. That’s why you and your staff must adhere to these security best practices. Fortify […]
Do you need identity and access management?

To defend against cyberthreats, businesses often implement strong antivirus software and firewalls — but both these solutions are not enough. A cutting-edge identity and access management (IAM) solution is crucial to protecting your digital assets from hackers, rogue employees, and weak passwords. What is IAM? Identity and access management is a system that secures, stores, […]
This malware can easily slip through Windows 10 security

Sophos researchers are warning Windows 10 users about a new type of malware that can disable and bypass computers’ security software. Known as Snatch, this ransomware is comprised of a collection of tools, including a separate data stealer. Designed to target businesses, this ransomware forces your Windows PC to reboot in Safe Mode to prevent […]
Make site visitors feel secure with these tips

Don’t give your customers any reason to feel insecure when dealing with you. When they visit and use your website, you must engender feelings of trust and security instead of alarm and distrust. Don’t worry — you can easily improve feelings of internet security with these three tips. Tip #1: Use HTTPS Short for Hypertext […]
5 Ways systems can be breached

When it comes to business IT security, many small- to medium-sized businesses (SMBs) often struggle to protect their systems from various cyberattacks. While there are many things you can do to secure your IT infrastructure, being aware of common security threats will really help. Here are five common ways your systems can be breached. #1. […]
Three cybersecurity standards most businesses are missing
Cybersecurity has finally been elevated to a “standard” in the business world. A business of ANY size needs to have a cybersecurity as part of their basic business planning checklist. This is especially important for businesses that are in the 50-500 employee size range, as these groups often are utilizing processes, and tools that have […]
5 Tips for securing your email account

Email is one of the best things the internet has made possible. We use email to signup for websites, apply for jobs, make payments, and many more. But email users also run the risk of account hijacking, malware attacks, and other cyberthreats. To secure your emails, follow these crucial tips. Use separate email accounts Most […]
Your password may be poor — update it now

A password policy designed for federal agencies must be secure, right? Surprisingly, that hasn’t been the case, according to the National Institute of Standards and Technology (NIST). The NIST created many of the password best practices you probably loathe — the combination of letters, numbers, and special characters — but it now says those guidelines […]
5 Easy tips for preventing data breaches

Avoiding malware and online scams takes a lot of work. You have to treat every email with suspicion, manage a long list of convoluted passwords, and avoid public WiFi networks. Ideally, you follow several other cybersecurity best practices, but many users don’t believe they’re worth the time. If you’re one of those people, here are […]
IAM benefits for your business

Whether it be cloud, mobile, or on-premises, every technology you use stores certain confidential data that are accessed by your employees. So how do you guarantee the safety of said data from cyber threats like identity theft, phishing attacks and more? IAM is the answer. What is IAM? Identity and access management is a system […]
Multi-Factor Authentication

Another day, another technology acronym to learn. Today, we are talking about Multi-Factor Authentication (MFA). If you have ever used an ATM card, you have used MFA. The first “factor” is that you needed the card to put in the machine, the second, your PIN code. Finance has long enforced these types of MFA mechanisms […]